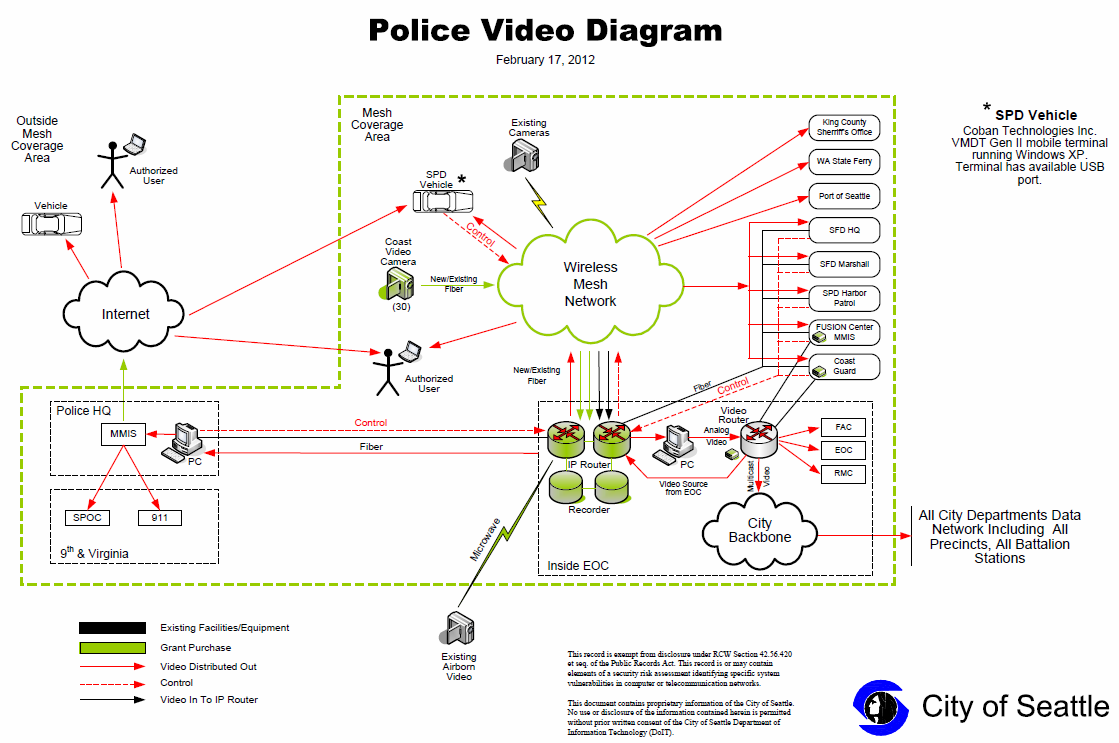
Part of the
Cisco Prime™ Infrastructure bundle, Cisco® Prime Network Control System (NCS) provides converged user, access, and identity management across wired and wireless networks to meet the challenges that Bring Your Own Device (BYOD) is placing on IT organizations. Designed with users and their mobile devices in mind, Cisco Prime NCS speeds network troubleshooting by giving IT complete visibility into connectivity, regardless of device, network or location. Deep integration with the
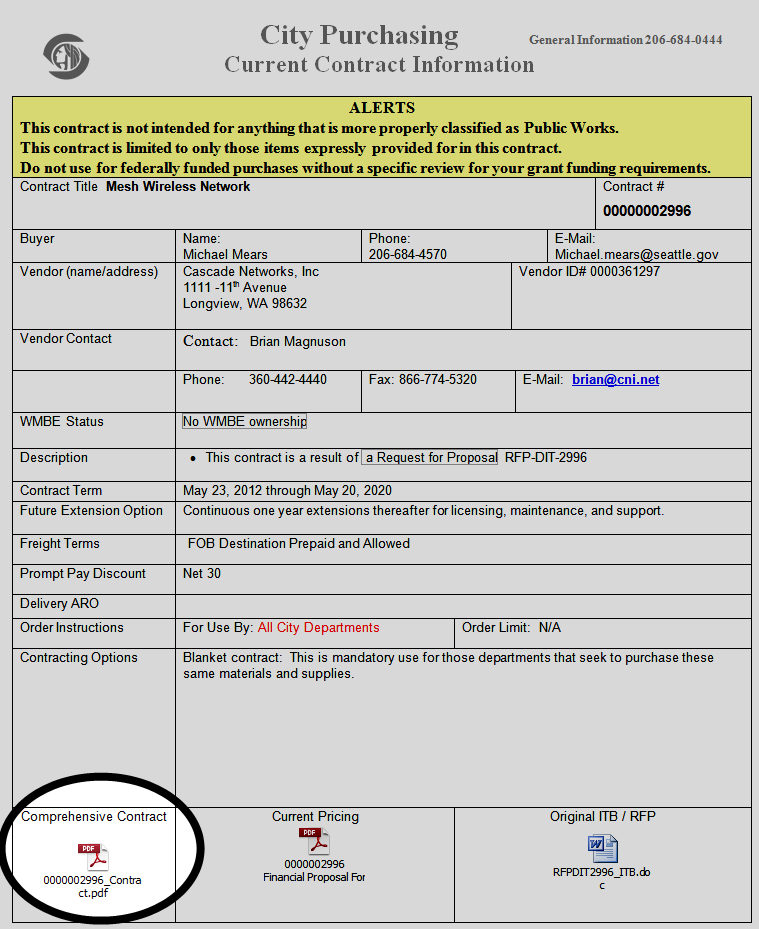
Cisco Identity Services Engine (ISE) further extends this visibility across security and policy-related problems, presenting a complete view of client issues with a clear path to solving them. Cisco Prime NCS (Figure 1) delivers full lifecycle management of Cisco
wireless LAN infrastructure, with additional focus on the deployment and management of branch networks.
Figure 1. Cisco Prime Network Control System
The platform significantly reduces operational costs by eliminating the need for competing overlay management solutions for wired, wireless, and branch networks, as well as security policy. Built on the foundation of Cisco Wireless Control System (WCS), Cisco Prime NCS:
• Helps resolve access problems across wired and wireless networks to get users back online faster
• Facilitates visibility of user attributes, posture, and profile through integration with the
Cisco Identity Services Engine (ISE)
• Introduces lifecycle management of Cisco Integrated Services Routers (ISRs), the Cisco Aggregation Services Router (ASR) 1000 Series, and Cisco Catalyst® switches
• Enables simplified deployment of branch offices requiring common, standardized configurations
• Allows full wireless lifecycle management, enabling IT staff to design and maintain optimal RF environments
• Offers an intuitive user experience to eliminate complexity, improve IT productivity, and minimize staffing requirements
• Provides a scalable platform for small, mid-sized, and large-scale wired and wireless networks, across both campus and distributed branch environments
• Delivers physical or virtual appliance deployment for flexibility without sacrificing functionality

Seamless Scalability
Cisco Prime NCS scales to manage thousands of routers and switches, hundreds of Cisco
wireless controllers, which in turn can manage up to 15,000 Cisco Aironet®
access points, including the next-generation, 802.11 Cisco Aironet 3600, 3500, 1040, 1260, 1250, and 1140 Series and OfficeExtend 600 Series. Cisco Prime NCS supports the Cisco Integrated Services Routers (ISRs), the Cisco Aggregation Services Router (ASR) 1000 Series, and Cisco Catalyst switches.
Cisco Prime NCS offers both physical appliance and virtual appliance deployment options, providing full product functionality, scalability, ease of installation, and setup tailored to your deployment preference.

WLAN Services Management
The platform provides complete WLAN services management, supporting:
• Cisco
CleanAir™ technology, a systemwide capability of the Cisco Unified Wireless Network providing proactive, high-speed spectrum intelligence to combat performance problems due to RF interference
• Cisco ISE integration, which allows for visibility into user and endpoint attributes, their posture, and profiling information for both wired and wireless clients
•
Integration with the Cisco Mobility Services Engine (MSE), which enables Cisco Context-Aware Software for real-time location tracking and local services discovery, along with Cisco Adaptive Wireless IPS (wIPS) Software for detection, containment, and location of security threats
These advanced mobility services provide additional information to the popular Client Troubleshooting tool, allowing quick problem resolution across any access medium.
Comprehensive Wireless LAN Lifecycle Management
Cisco Prime NCS cost-effectively supports all phases of the wireless LAN lifecycle from planning and deployment, to monitoring, troubleshooting, and customized reporting. Cisco Prime NCS allows wireless LAN operations to be more efficient and effective for all lifecycle phases (Figure 2).
Figure 2. Comprehensive Wireless LAN Lifecycle Management
Planning
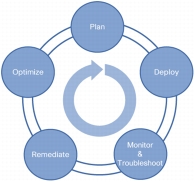
Designing a wireless LAN that effectively supports business-critical data, voice, and video services is simplified with the Cisco Prime NCS suite of built-in planning and design tools (Figure 3).
Figure 3. Simplified Wireless LAN Planning and Design
The planning and design tools in Cisco Prime NCS simplify the process of defining access point placement and determining access point coverage areas for standard and irregularly shaped buildings. These tools give IT administrators clear visibility into the RF environment to anticipate future coverage needs, assess wireless LAN events, and mitigate or eliminate improper RF designs and coverage problems.
Specialized Cisco Prime NCS planning tools facilitate immediate assessment of the WLAN's readiness to provide voice-over-WLAN services supporting single and dual-mode Wi-Fi-enabled phones, and context-aware (location) services that use Cisco's patent-pending "RF fingerprinting" technology to locate, track, and manage Wi-Fi-enabled devices and their contextual information in conjunction with Cisco MSE.
Deployment
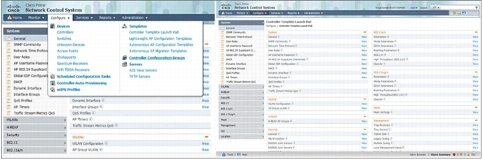
Getting the wireless LAN up and running quickly and cost-effectively to meet end-user needs is streamlined with the broad array of Cisco Prime NCS integrated configuration templates. Flexible, easy-to-use templates and deployment tools - such as the Controller Auto-Provisioning feature for zero-touch deployment of Cisco Wireless LAN Controllers - help IT managers provision and configure the wireless LAN to expressly deliver the services that their business requires (Figure 4). These templates and tools make it simple to apply common and best-practices configurations across multiple wireless LAN controllers regardless of their location, streamlining even the most complex controller configurations, updates, and scheduling. Provisioning access points is just as simple with easy-to-use templates for customized configuration of multiple access points.
Figure 4. Flexible Deployment Tools and Configuration Templates
Monitoring and Troubleshooting
Cisco Prime NCS is the ideal management platform for monitoring and troubleshooting the wired and wireless LAN to maintain robust performance and deliver an optimal access experience to fixed and mobile endpoints. The centralized interface of Cisco Prime NCS makes it easy to access information where it's needed, when it's needed, on-demand or as scheduled.
The easy-to-use graphical display serves as a starting point for maintenance, security, troubleshooting, and future capacity planning activities. Quick access to actionable data about healthy and unhealthy devices is available from a variety of entry points, making Cisco Prime NCS vital to ongoing network operations.
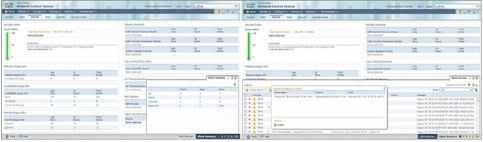
The ever-present alarm summary panel and alarm browser in Cisco Prime NCS simplify access to critical information, faults, and alarms based on their severity (Figure 5). The alarm summary panel facilitates faster assessment of outstanding notifications and supports quicker resolution of trouble tickets. Detecting, locating, and containing unauthorized (rogue) devices are fully supported when location services are enabled.
Figure 5. Ever-Present Alarm Summary and Alarm Browser Interaction
The integrated workflows and extensive array of troubleshooting tools in Cisco Prime NCS help IT administrators quickly identify, isolate, and resolve problems across all components of the Cisco access network. Cisco NCS supports rapid troubleshooting of LANs and WLANs of any size with minimal IT staffing. A set of tools works together to help IT administrators understand the operational nuances occurring on the LAN and WLAN and discover nonoptimal events occurring outside baseline parameters (for example, client connection or roaming problems):
• The ever-present search tool facilitates cross-network access to immediate and historic information about devices and assets located anywhere in the access network, including endpoint and session attributes, association history, endpoint location, RF performance, statistics, radio resource management (RRM), and air quality.
• Integrated workflows support seamless linkage between all tools, alarms, alerts, searches, and reports for all infrastructure components and client devices.
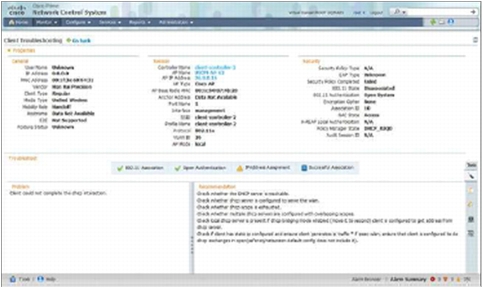
• A built-in Client Troubleshooting tool provides a step-by-step method to analyze problems for all wired and wireless client devices. This robust Client Troubleshooting tool helps reduce operating costs by speeding the resolution of trouble tickets for a variety of Wi-Fi client device types. The tool can also assist with client trending analysis (Figure 6).
• When Cisco Compatible Extensions clients, Cisco ISE, and Cisco CleanAir technology are used, specialized diagnostic tools are available to support enhanced analysis of connection problems.
Figure 6. Built-in Client Troubleshooting Tool to Support Step-by-Step Problem Analysis
Remediation
Cisco Prime NCS makes it easy to quickly assess service disruptions, receive notices about performance degradation, research resolutions, and take action to remedy nonoptimal situations.
•
Cisco CleanAir technology supports finding, classifying, correlating, and mitigating interference from Wi-Fi and non-Wi-Fi sources such as rogue access points, microwave ovens, Bluetooth devices, and cordless phones. Cisco CleanAir technology improves air quality and creates a self-healing and self-optimizing wireless network that mitigates the impact of wireless interference sources.
• Built-in tools such as the Client Troubleshooting tool support help desk staff and level-two administrators resolve client access issues by providing guidance on where the actual problem may be.
• The security dashboard allows for a network-level assessment and provides a security index with suggestions on how to improve security across your deployment.
• The voice-service audit tool not only provides a way to audit the current network configuration for voice over wireless LAN (VoWLAN) deployments, but also provides a way to rectify the current configuration based on Cisco best practices for VoWLAN deployment.
Optimization
Cisco Prime NCS includes customizable reporting that assists IT teams to effectively manage, maintain, and evolve the wireless LAN to meet ongoing business and operations requirements. In addition to tools such as configuration compliance monitoring with comprehensive auditing functionality, flexible reports provide access to the right data, at the right time, in a format to meet any requirement (Figure 7).