Mike Lindell, aka "The My Pillow Guy" is a Trump supporter who thinks there was massive election Fraud, and he's created a 2-hour video attempting to demonstrate this. It was broadcast, at his own expense, on OAN (a right-of-Fox cable news channel). It can be viewed in full on Lindell's personal web page (https://michaeljlindell.com/). It was posted on YouTube, but removed after a few hours.
I have not watched it all, but it appears to be a lots of similar things that were shown before. At one point, the apparent money shot of the video, he says there is "100% Proof" of a cyber attack, and brings on Mary Fanning by phone. (1h 36m), since this seems like the focus of the video, it's probably a good place to start.
She shows a list of what she describes as hacking.
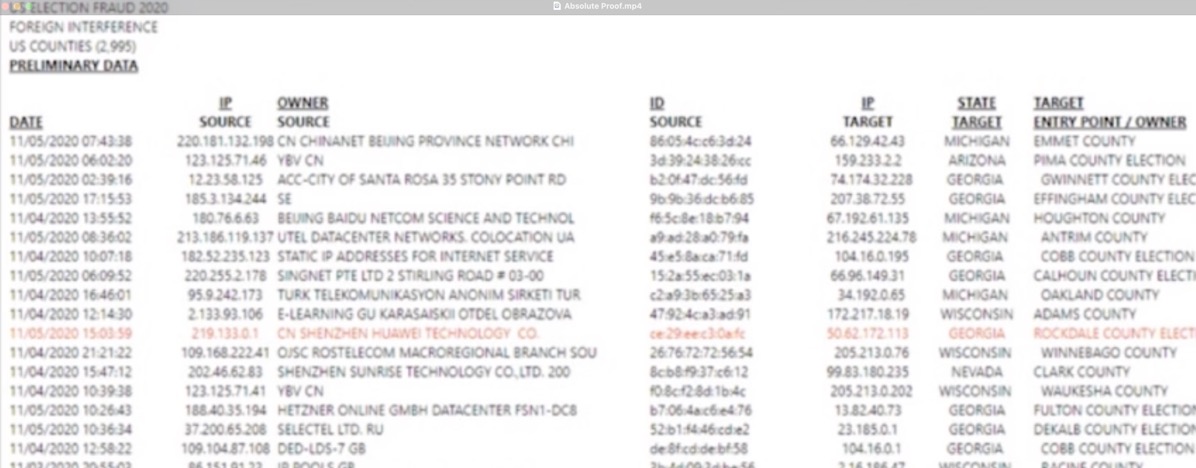
It's a time-stamped list of supposed source and targets of some kind of connection. It's not clear how this was obtained.
Each line is linked with a "Method of Intrusion and a "Votes changed"
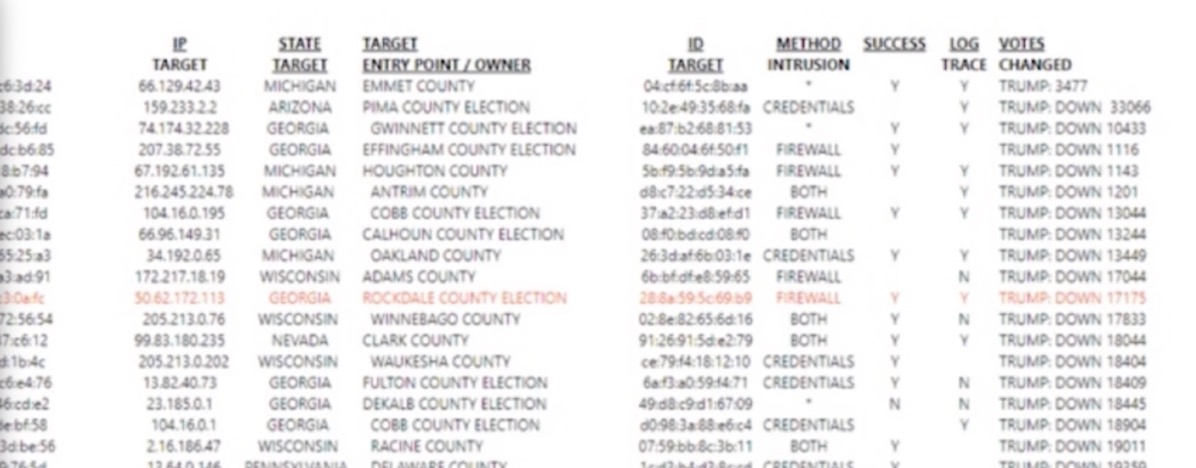
Lindell cites this as 100% proof, which is a bit bemusing, as there's no actual evidence of these intrusions or the "stealing" of votes. It's not documentation, it's not evidence, it's a claim - or rather, it's lots of little claims. Any one of which, if true, would be foreign interference in the election. None of these claims are backed by any evidence.
The presentation seems nonsensical. There's a column listing if the attack was successful, which is either Yes, No, or blank. Regardless of the value in this column, there's an entry in the "Votes Changed" column.
The entries are weird, in that they (and presumably the entire spreadsheet) seems to have been sorted alphabetically, which makes no sense at all - possibly a failed attempt to put the biggest numbers on the first page.
They then show an animation, with moving dots that are apparently "the actual files that are being moved and sent"
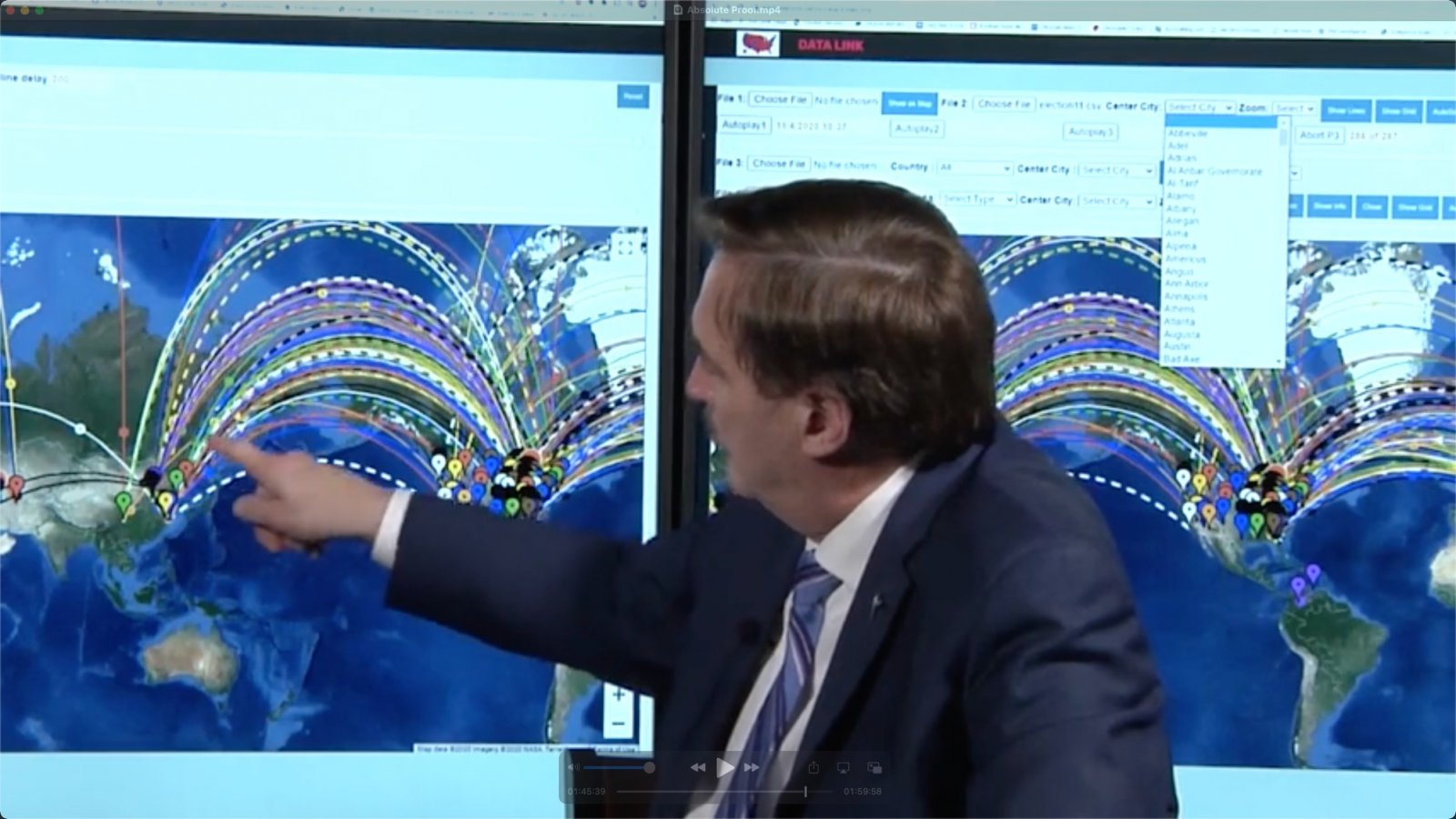
No information as to what is in these "files", of how they know.
She mentioned "prismatic scoring algorithms" stealing the votes at "the transfer points".
This huge dump of vague data seems rather pointless, what you need is ONE demonstration of a foreign attack. Take the first line of that spreadsheet, demonstrate how you got these numbers, and how you know it caused the vote to be changed.
The bottom line here is that this is just a spreadsheet, with no evidence that it's actually what they claim it to be.
I have not watched it all, but it appears to be a lots of similar things that were shown before. At one point, the apparent money shot of the video, he says there is "100% Proof" of a cyber attack, and brings on Mary Fanning by phone. (1h 36m), since this seems like the focus of the video, it's probably a good place to start.
She shows a list of what she describes as hacking.
It's a time-stamped list of supposed source and targets of some kind of connection. It's not clear how this was obtained.
Each line is linked with a "Method of Intrusion and a "Votes changed"
Lindell cites this as 100% proof, which is a bit bemusing, as there's no actual evidence of these intrusions or the "stealing" of votes. It's not documentation, it's not evidence, it's a claim - or rather, it's lots of little claims. Any one of which, if true, would be foreign interference in the election. None of these claims are backed by any evidence.
The presentation seems nonsensical. There's a column listing if the attack was successful, which is either Yes, No, or blank. Regardless of the value in this column, there's an entry in the "Votes Changed" column.
The entries are weird, in that they (and presumably the entire spreadsheet) seems to have been sorted alphabetically, which makes no sense at all - possibly a failed attempt to put the biggest numbers on the first page.
They then show an animation, with moving dots that are apparently "the actual files that are being moved and sent"
No information as to what is in these "files", of how they know.
She mentioned "prismatic scoring algorithms" stealing the votes at "the transfer points".
This huge dump of vague data seems rather pointless, what you need is ONE demonstration of a foreign attack. Take the first line of that spreadsheet, demonstrate how you got these numbers, and how you know it caused the vote to be changed.
The bottom line here is that this is just a spreadsheet, with no evidence that it's actually what they claim it to be.
Last edited:
