John J.
Senior Member.
[Admin: thread split from: https://www.metabunk.org/threads/mi...served-apparent-spherical-uap-via-aaro.12932/ ]
Just to "throw something out there" which might be worth considering (or not),
...and to get my apologies in in advance,
(1) I don't think the following suggestion is a likely explanation of the "sphere"
(2) The possibility of, e.g., a metallicized balloon seems a better, simpler explanation as far as I can tell
(3) I have no special knowledge of UAVs/ camera technology/ electronic or cyber warfare
(4)-Meaning that, I accept the following idea might be obviously implausible to you chaps and chapesses with knowledge of these things
(5) The following idea does involve the "multiplication of entities" and so falls foul of Occam's razor (unless it is the simplest explanation covering all the relevant facts, which is probably unlikely)
Is it possible that the "sphere" is not a physical object being viewed by the RPV, but the result of deliberate interference with the feed to the RPV operators?
Something like this:
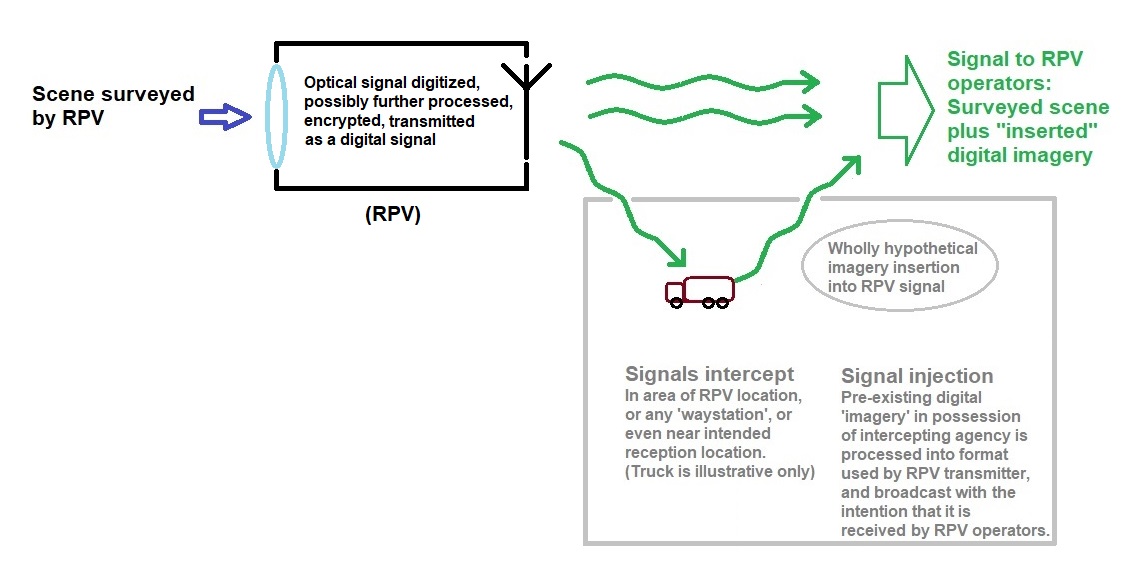
We know that a US drone has been successfully "hacked" by the Iranian military
https://en.wikipedia.org/wiki/Iran–U.S._RQ-170_incident (Wikipedia article describing the in-flight capture of a US RQ-170 Sentinel drone by Iran, 05/12/2011).
The Iranian authorities later claimed to have decrypted the footage taken by that drone
(BBC news item, https://www.bbc.co.uk/news/world-middle-east-21373353, "Iran shows 'hacked US spy drone' video footage",
07/02/13).
I would have thought that signals to and from the drone are encrypted, nevertheless Iranian personnel were able to overcome this. I doubt if Iran is a leading state in cryptoanalysis or EW.
We're used to hearing about encoding algorithms whose products would take vast lengths of time to decrypt, but nevertheless various actors seem to actively research additional encryption methods- implying that perhaps some interested parties don't think that existing encryption packages are quite as secure as they're said to be.
There are, I guess, ways of cutting down the "problem space" of decrypting a drone's transmissions. For example, knowledge of the resolution (as in "x" by "y" pixels) and frame rate of any video being transmitted might help.
And, of course, you might access the appropriate decryption technology via espionage.
There are obvious tactical advantages to being able to interfere with a drone's video signal.
Your assets "in the field" might be masked, or (virtually) added to.
Most people (in the west) are aware that photos, and increasingly video, can be doctored. Showing the original (authentic) image or video is often an effective rebuttal. However, this would be difficult if the video feed you receive from your drone shows (e.g.) a (CGI) school bus driving into an area just as your munitions detonate.
Hypothetically, why might a party testing an "imagery insertion" capability use a "UFO"?
Well, that party might not be in a position to see, with certainty, what the RPV operators actually receive.
(1) Faking a mundane item- say, a bicycle leaning against a lamppost- is unlikely to generate much interest. You won't know if the RPV operator has seen it or not.
(2) Imagery of obvious interest- maybe a pickup carrying man-portable AA missiles- might generate too much interest if you're testing a nascent capability which doesn't allow alteration of your feed in real time. E.g., the RPV operators might engage, and then be suspicious when the target is unaffected.
(3) A "UFO" might get the attention of the drone operator.
It is apparent, from material in the public realm, that US aircrew [in fairness, probably all aircrew worth their salt] pay attention to "UFOs", and that such sightings generate much chatter. The same might apply to RPV operators.
Footage of "UFOs" taken by US aircraft has tended to end up in the public realm in recent years.
An agency testing a (hypothetical) capability of this sort would get invaluable feedback- possibly including footage as received by the RPV operator.
Of course, this might all be ridiculous, I "don't know what I don't know" to paraphrase Mr Rumsfeld.
If you work in the Chinese embassy or intelligence service- clearly we don't really think you're anywhere near developing such a complex capability- if you know better, post your proof here, please.
Just to "throw something out there" which might be worth considering (or not),
...and to get my apologies in in advance,
(1) I don't think the following suggestion is a likely explanation of the "sphere"
(2) The possibility of, e.g., a metallicized balloon seems a better, simpler explanation as far as I can tell
(3) I have no special knowledge of UAVs/ camera technology/ electronic or cyber warfare
(4)-Meaning that, I accept the following idea might be obviously implausible to you chaps and chapesses with knowledge of these things
(5) The following idea does involve the "multiplication of entities" and so falls foul of Occam's razor (unless it is the simplest explanation covering all the relevant facts, which is probably unlikely)
Is it possible that the "sphere" is not a physical object being viewed by the RPV, but the result of deliberate interference with the feed to the RPV operators?
Something like this:
We know that a US drone has been successfully "hacked" by the Iranian military
https://en.wikipedia.org/wiki/Iran–U.S._RQ-170_incident (Wikipedia article describing the in-flight capture of a US RQ-170 Sentinel drone by Iran, 05/12/2011).
The Iranian authorities later claimed to have decrypted the footage taken by that drone
(BBC news item, https://www.bbc.co.uk/news/world-middle-east-21373353, "Iran shows 'hacked US spy drone' video footage",
07/02/13).
I would have thought that signals to and from the drone are encrypted, nevertheless Iranian personnel were able to overcome this. I doubt if Iran is a leading state in cryptoanalysis or EW.
We're used to hearing about encoding algorithms whose products would take vast lengths of time to decrypt, but nevertheless various actors seem to actively research additional encryption methods- implying that perhaps some interested parties don't think that existing encryption packages are quite as secure as they're said to be.
There are, I guess, ways of cutting down the "problem space" of decrypting a drone's transmissions. For example, knowledge of the resolution (as in "x" by "y" pixels) and frame rate of any video being transmitted might help.
And, of course, you might access the appropriate decryption technology via espionage.
There are obvious tactical advantages to being able to interfere with a drone's video signal.
Your assets "in the field" might be masked, or (virtually) added to.
Most people (in the west) are aware that photos, and increasingly video, can be doctored. Showing the original (authentic) image or video is often an effective rebuttal. However, this would be difficult if the video feed you receive from your drone shows (e.g.) a (CGI) school bus driving into an area just as your munitions detonate.
Hypothetically, why might a party testing an "imagery insertion" capability use a "UFO"?
Well, that party might not be in a position to see, with certainty, what the RPV operators actually receive.
(1) Faking a mundane item- say, a bicycle leaning against a lamppost- is unlikely to generate much interest. You won't know if the RPV operator has seen it or not.
(2) Imagery of obvious interest- maybe a pickup carrying man-portable AA missiles- might generate too much interest if you're testing a nascent capability which doesn't allow alteration of your feed in real time. E.g., the RPV operators might engage, and then be suspicious when the target is unaffected.
(3) A "UFO" might get the attention of the drone operator.
It is apparent, from material in the public realm, that US aircrew [in fairness, probably all aircrew worth their salt] pay attention to "UFOs", and that such sightings generate much chatter. The same might apply to RPV operators.
Footage of "UFOs" taken by US aircraft has tended to end up in the public realm in recent years.
An agency testing a (hypothetical) capability of this sort would get invaluable feedback- possibly including footage as received by the RPV operator.
Of course, this might all be ridiculous, I "don't know what I don't know" to paraphrase Mr Rumsfeld.
If you work in the Chinese embassy or intelligence service- clearly we don't really think you're anywhere near developing such a complex capability- if you know better, post your proof here, please.
Last edited by a moderator:
